获取域/子域名列表,并探测http/https服务器的工具:FProbe
- 发表于
- 安全工具
FProbe
一个快速HTTP探测工具,可用于信息收集等场景,使用GO编写。更多类似的工具你可以在Hacking Tools里找到。
功能特征
- 获取域/子域名列表,并探查工作中的http/https服务器。
- 在运行时优化RAM和CPU。
- 支持每个域的特殊端口
- 附加头详细信息,比如JSON的
Status Code,Content Type,Location。
安装
|
1 |
GO111MODULE=on go get -u github.com/theblackturtle/fprobe |
用法
|
1 2 3 4 5 6 7 8 9 10 11 12 |
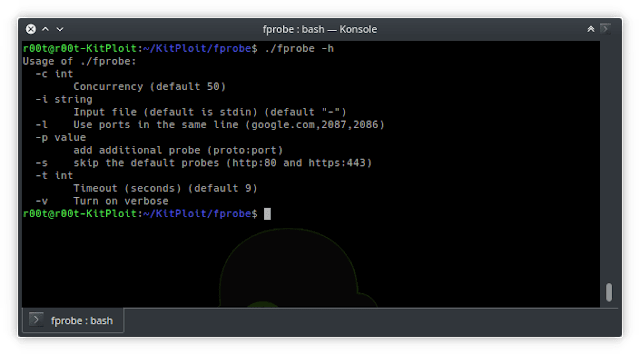
Usage of fprobe: -c int Concurrency (default 50) -i string Input file (default is stdin) (default "-") -l Use ports in the same line (google.com,2087,2086) -p value add additional probe (proto:port) -s skip the default probes (http:80 and https:443) -t int Timeout (seconds) (default 9) -v Turn on verbose |
基本用法
标准输入
|
1 |
❯ cat domains.txt | fprobe |
文件输入
|
1 |
❯ fprobe -i domains.txt |
并发
|
1 |
❯ cat domains.txt | fprobe -c 200 |
使用内联端口
如果要对每个域使用特殊端口,则可以使用该-l标志。您可以解析Nmap / Masscan输出并将其重新格式化以使用此功能。
输入(domains.txt)
|
1 2 3 |
google.com,2087,2086,8880,2082,443,80,2052,2096,2083,8080,8443,2095,2053 yahoo.com,2087,2086,8880,2082,443,80,2052,2096,2083,8080,8443,2095,2053 sport.yahoo.com,2086,443,2096,2053,8080,2082,80,2083,8443,2052,2087,2095,8880 |
命令
|
1 |
❯ cat domains.txt | fprobe -l |
暂停
|
1 |
❯ cat domains.txt | fprobe -t 10 |
特殊端口
|
1 |
❯ cat domains.txt | fprobe -p http:8080 -p https:8443 |
检查网址
|
1 2 3 |
❯ echo 'https://google.com/path1?param=1' | fprobe https://google.com/path1?param=1 |
使用内置端口集合(默认情况下包括80、443)
- 中:8000,8080,8443
- 大型:81、591、2082、2087、2095、2096、3000、8000、8001、8008、8080、8083、8443、8834、8888
- XLarge:81,300,591,593,832,981,1010,1311,2082,2087,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108, 5800,6543,7000,7396,7474,8000,8001,8008,8014,8042,8069,8080,8081,8088,8090,8091,8118,8123,8172,8222,8243,8280,8281,8333,8443, 8500,8834,8880,8888,8983,9000,9043,9060,9080,9090,9091,9200,9443,9800,9981,12443,16080,18091、18092、20720、28017
|
1 |
❯ cat domains.txt | fprobe -p medium/large/xlarge |
跳过默认探针
如果您不想探测端口80上的HTTP或端口443上的HTTPS,则可以使用该-s标志。
|
1 |
❯ cat domains.txt | fprobe -s |
详细
详细输出一些附加头,诸如JSON格式格式Status Code,Content Type,Location。
|
1 |
❯ cat domains.txt | fprobe -v |
|
1 2 |
{"site":"http://google.com","status_code":301,"server":"gws","content_type":"text/html; charset=UTF-8","location":"http://www.google.com/"} {"site":"https://google.com","status_code":301,"server":"gws","content_type":"text/html; charset=UTF-8","location":"https://www.google.com/"} |
原文连接:获取域/子域名列表,并探测http/https服务器的工具:FProbe
所有媒体,可在保留署名、
原文连接的情况下转载,若非则不得使用我方内容。